Courses
How To Hack Instagram Account Using Social Engineering techniques
Have you ever wondered how hackers trick people into giving away their Instagram passwords? This course provides a complete, step-by-step guide to understanding these techniques for ethical purposes. You’ll gain practical knowledge of phishing, email spoofing, and social engineering tactics, so you can recognize and defend against these methods in real life.
What You’ll Learn:
Understanding Phishing Pages Phishing pages are fake websites designed to look exactly like Instagram’s login page. Hackers use these pages to trick people into entering their usernames and passwords.
We’ll teach you how to create a phishing page using a tool we provide. This tool makes the process straightforward, even if you’re new to ethical hacking.
For those who want a more hands-on approach, we’ll guide you through manually creating a phishing page from scratch. This will give you a deeper understanding of how these attacks are set up.
Crafting Fake Emails (Email Spoofing) To convince someone to visit a phishing page, hackers often send fake emails that appear to be from Instagram. These emails create a sense of urgency, prompting the target to act quickly.
You’ll learn how to craft these emails using techniques to make them look legitimate, such as masking the sender to appear like Instagram.
We’ll guide you step-by-step in replicating Instagram’s official email style to make your emails more convincing.
Sending Fake Login Alerts and OTPs To increase the target’s panic and likelihood of falling for the phishing attempt, hackers often send fake One-Time Password (OTP) notifications.
We’ll show you how to use our tool to send OTP messages that make the victim believe someone is attempting to log into their Instagram account.
The victim will see this message and think they need to act immediately to secure their account, leading them to interact with the phishing page.
Social Engineering Fundamentals Before diving into simulations, we’ll explore the basics of social engineering, the psychological techniques hackers use to manipulate their targets.
You’ll learn about tactics like creating urgency, building trust, and exploiting human errors.
Understanding these principles will help you grasp why people fall for these scams and how to prevent them.
Simulating a Social Engineering Attack After mastering phishing pages, emails, and OTPs, we’ll show you how to combine them into a realistic simulation.
You’ll create an email alert warning the target that their Instagram account was accessed from an unknown location.
This alert directs them to the phishing page you built. When they attempt to “reset” their password on the phishing page, their login credentials (username and password) will be captured.
See the Method in Shot: How Social Engineering Hacks Instagram
What You'll Learn
Our course is structured into nine practical video tutorials, each approximately 10 minutes long, covering the following topics:
Part-1: Installing Termux: Learn how to set up Termux, a powerful terminal emulator for Android, and prepare your environment for hacking.
Part-2: Setting Up and Creating a Phishing Page: Step-by-step guidance on creating your first phishing page.
Part-3: Advanced Phishing Page Techniques: Dive deeper into advanced techniques for creating more convincing phishing pages.
Part-4: Creating a Cloudflared Server for Port Forwarding: Set up a Cloudflared server to facilitate port forwarding and enhance your phishing attacks.
Part-5: Manually Creating a Phishing Page: Master the art of manually crafting phishing pages for better control and customisation.
Part-6: Manipulating Victims with OTP Messages: Learn how to send OTP messages to manipulate your target before sending a cloned Instagram email.
Part-7: Creating a Fake Gmail Account: Create and use fake Gmail accounts to enhance your phishing schemes.
Part-8: Creating a Cloned Instagram Email: Design and send convincing cloned Instagram emails to your targets.
Part-9: Binding Phishing Links in Cloned Emails: Seamlessly integrate phishing links into your cloned Instagram emails for maximum effectiveness.
Course Features
50+ Phishing Templates: Gain access to a comprehensive library of phishing templates to kickstart your hacking efforts.
Powerful Hacking Tools: Utilize powerful tools provided in the course to enhance your hacking skills.
Command Line Mastery: Receive all command lines in .txt files for easy reference and practice.
Hands-on Learning: Engage in practical exercises designed to provide real-world hacking experience.
Outcomes
By the end of this course, you will have a thorough understanding of how real hackers exploit social engineering techniques to hack Instagram accounts. You'll gain practical experience and valuable insights into the world of ethical hacking.
Enroll now to elevate your hacking skills and explore the fascinating world of social engineering!
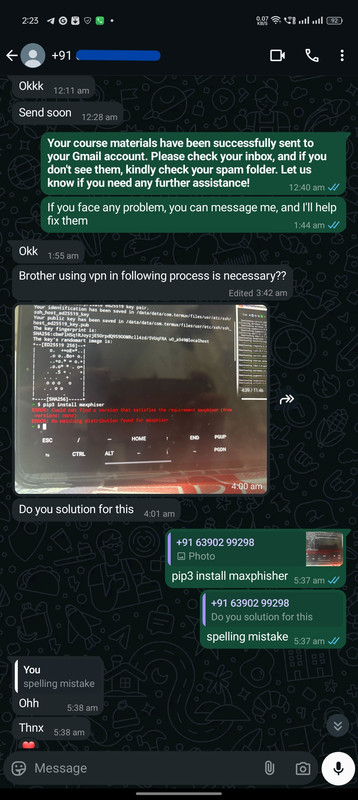
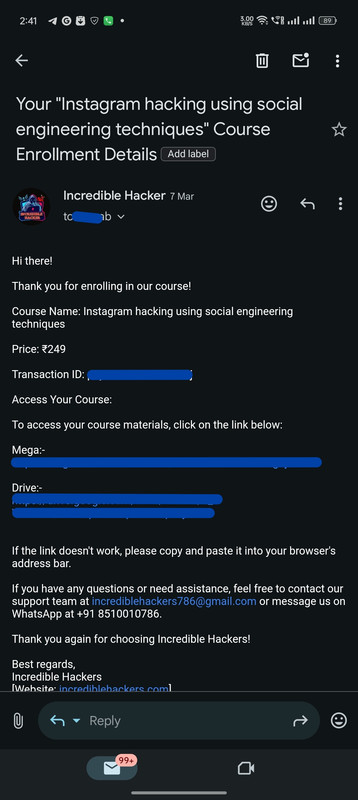
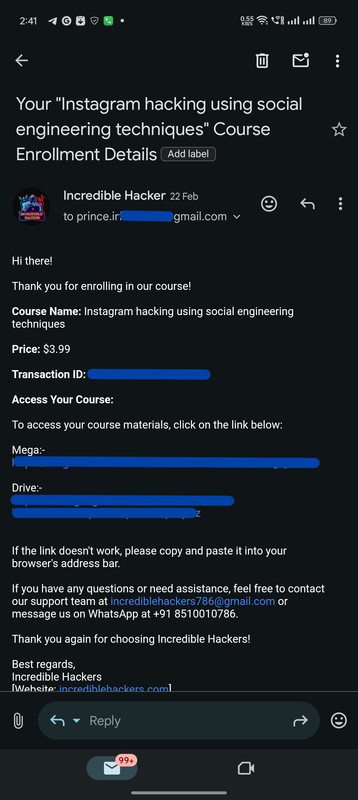
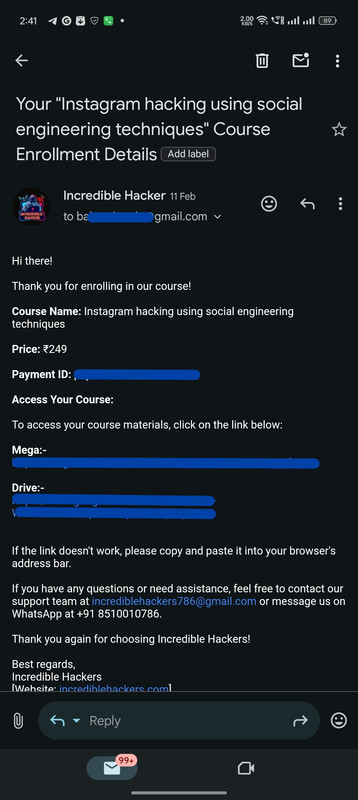
Real Customers, Real Courses: Proof of Enrollment
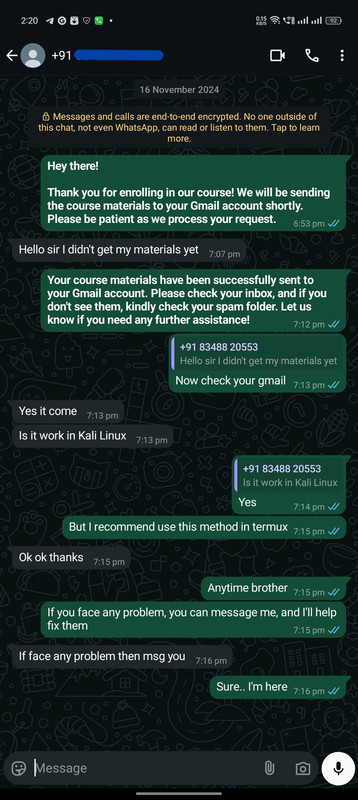
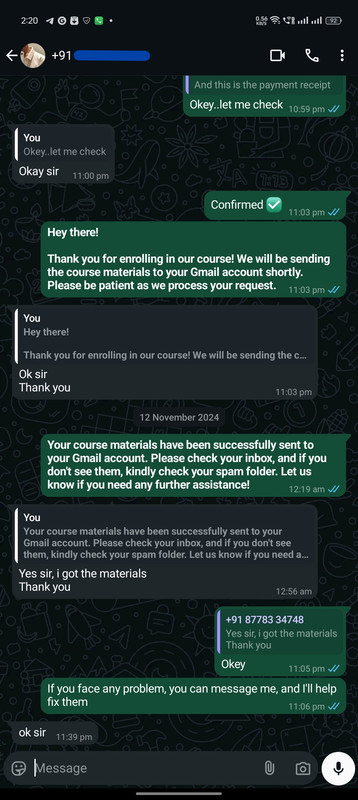
Instant Confirmation: Here's How We Deliver Your Course
Disclaimer:This course is intended for educational purposes only. Always practice ethical hacking and ensure you have permission before attempting to hack any accounts.