Ebooks
🔍 Introduction
In today's digital age, Android stands as one of the most widely used mobile operating systems, powering billions of devices worldwide. With its open-source nature and extensive user base, Android presents both opportunities and challenges in the realm of cybersecurity. The Android Hacker's Handbook serves as an essential guide for security professionals, developers, and enthusiasts aiming to delve deep into Android's security architecture and uncover potential vulnerabilities.
📖 Detailed Summary
Authored by a team of renowned security experts—Joshua J. Drake, Zach Lanier, Collin Mulliner, Pau Oliva Fora, Stephen A. Ridley, and Georg Wicherski—this handbook offers a comprehensive exploration of Android's internal mechanisms. The book begins by providing an overview of the Android ecosystem, highlighting its growth, diversity, and the inherent security implications.
Book Index
Key topics covered include:
Android Security Architecture: An in-depth look at Android's security model, including its sandboxing techniques, permission systems, and the role of the Dalvik Virtual Machine.
Application Analysis: Techniques for both static and dynamic analysis of Android applications, enabling readers to identify and understand potential security flaws.
Rooting and Exploitation: A comprehensive guide to rooting Android devices, understanding partition layouts, and exploiting vulnerabilities within system components.
Reverse Engineering: Methods for decompiling and analyzing Android applications, providing insights into app behavior and potential security issues.
Real-World Case Studies: Detailed examinations of actual vulnerabilities and exploits, offering practical examples of security challenges and solutions.
Throughout the book, the authors emphasize practical approaches, equipping readers with the tools and knowledge necessary to assess and enhance Android security effectively.
🎯 Key Takeaways
Comprehensive Understanding: Gain a thorough grasp of Android's architecture and security mechanisms.
Analytical Skills: Develop the ability to perform both static and dynamic analyses of Android applications.
Exploitation Techniques: Learn how to identify and exploit vulnerabilities within the Android operating system.
Preventative Measures: Understand best practices for securing Android devices and applications against potential threats.
👤 Who Should Read This Book?
This handbook is tailored for:
Security Researchers: Looking to deepen their understanding of mobile security.
Android Developers: Aiming to build secure applications and understand potential vulnerabilities.
IT Professionals: Responsible for managing and securing Android devices within organizations.
Cybersecurity Enthusiasts: Interested in exploring the intricacies of Android security.
📚 Book Details
Authors: Joshua J. Drake, Zach Lanier, Collin Mulliner, Pau Oliva Fora, Stephen A. Ridley, Georg Wicherski
Publisher: Wiley
Publication Date: March 26, 2014
Pages: 576
ISBN: 978-1118608647
💡 Why This Book Matters
As mobile devices become increasingly integral to our daily lives, ensuring their security is paramount. The Android Hacker's Handbook provides readers with a deep understanding of Android's security landscape, offering both theoretical knowledge and practical tools to identify and mitigate potential threats. Whether you're a seasoned professional or a curious learner, this book serves as a valuable resource in the ever-evolving field of mobile security.
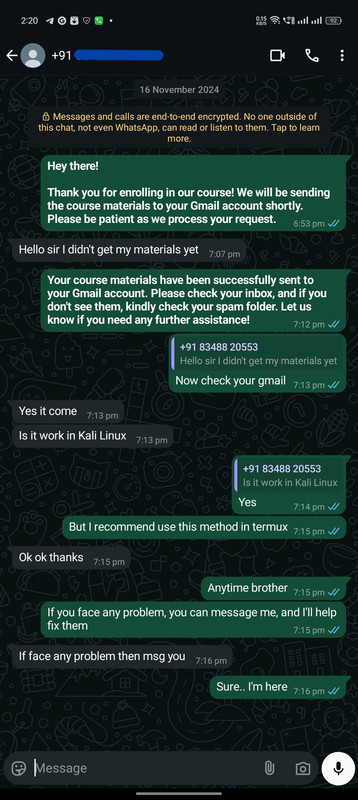
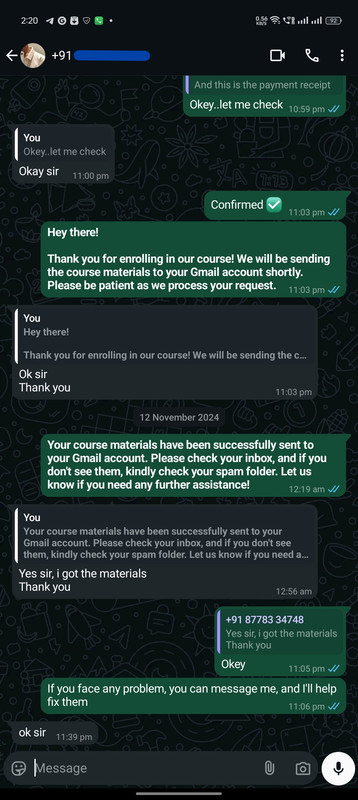
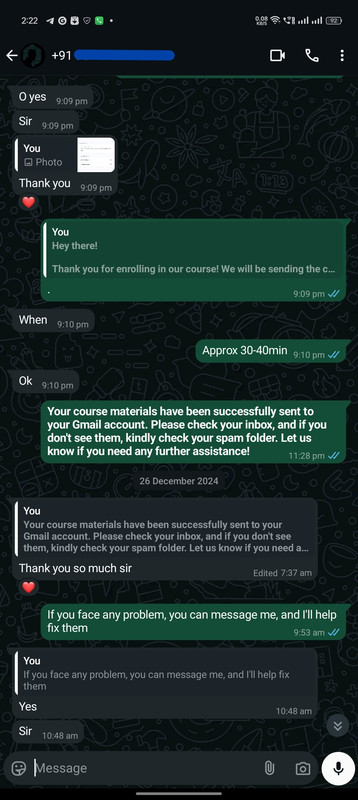
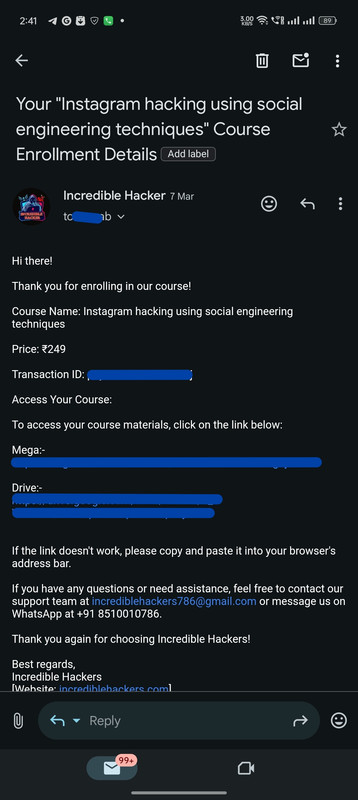
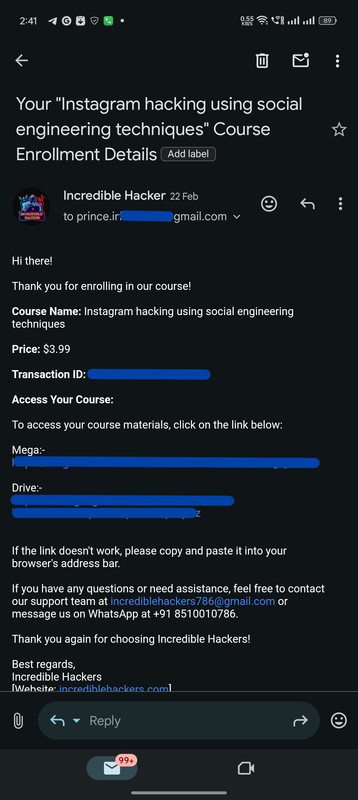
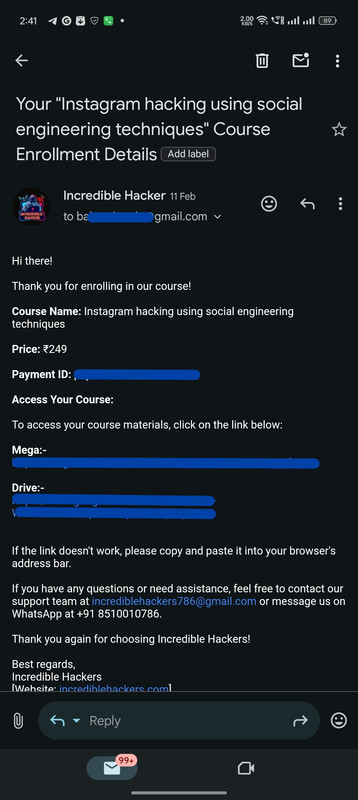
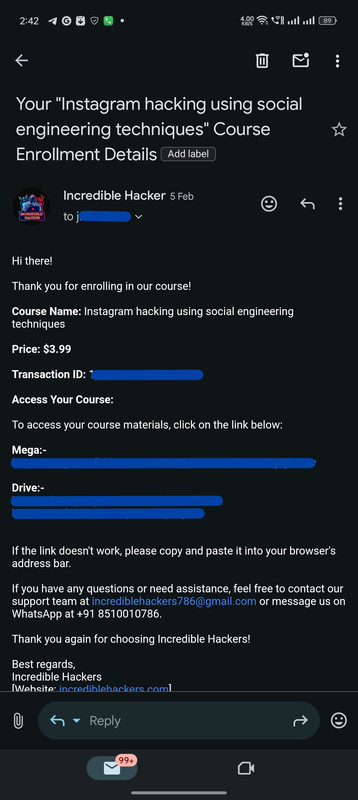
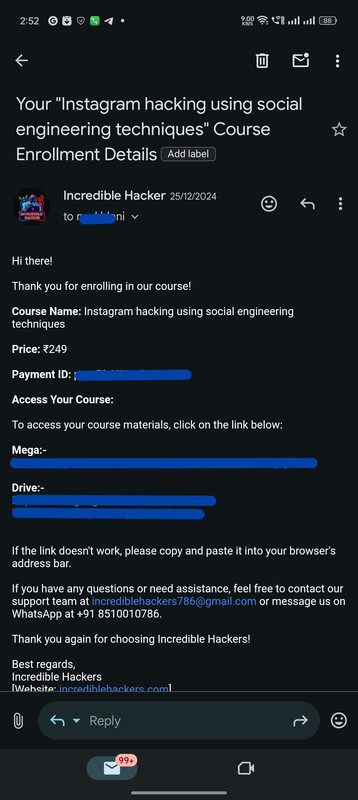
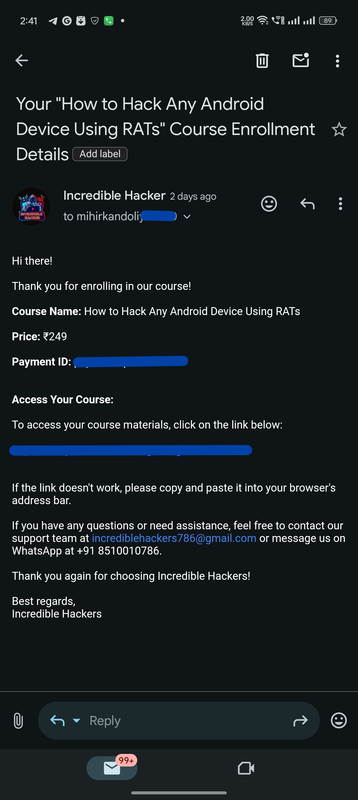
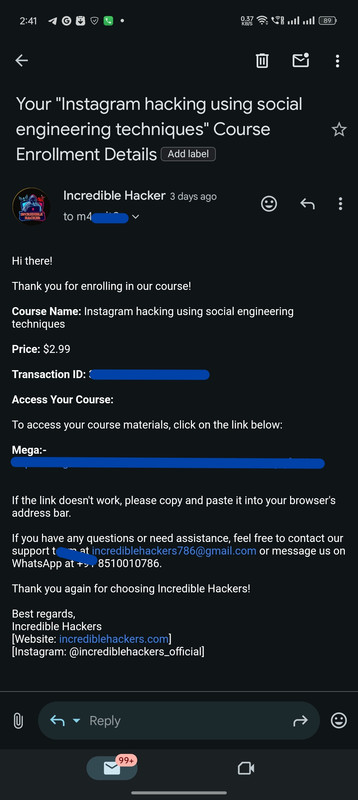
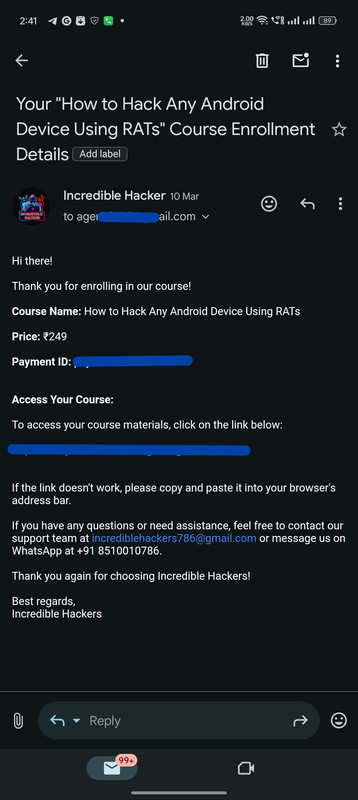
Real Customers, Real Courses: Proof of Enrollment
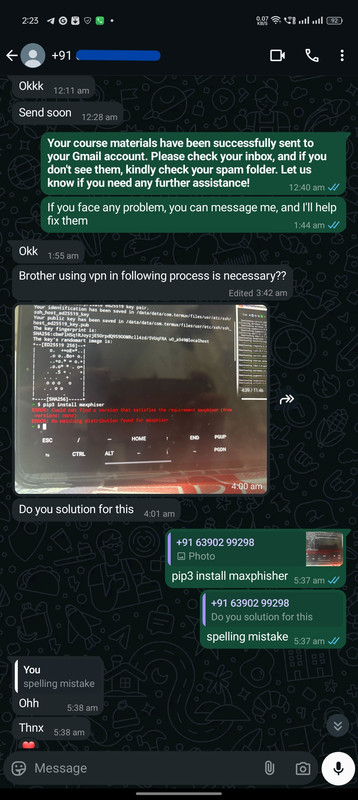
Instant Confirmation: Here's How We Deliver Your Course
Whether you are a cybersecurity enthusiast, a professional pentester, or simply curious about Android hacking, our Android Hacking Kit provides you with the tools and knowledge needed to explore and exploit Android devices with confidence.
Unlock the full potential of Android hacking today. Ready to take control? Start your digital journey with our Android Hacking Kit!
Confirm The Product
Selected Package → ₹249
Android Hacking using Rats
Explore Android Hacking: Gain hands-on experience using Remote Access Tools (RATS) to understand and secure Android systems effectively.